When an enterprise begins to implement a safety instrumentation system (SIS) project, one of the first decisions stakeholders must make is to choose a system architecture. Compliance with international cybersecurity standards, such as IEC 62443 (ANSI/ISA 62443 series standards) and the International Association of Process Industrial Automation Users (NAMUR) guidelines, makes it possible to enhance systems with an interface or integrated SIS architecture. Understanding the unique advantages and considerations behind each architecture is critical to making informed decisions that best meet the needs of the enterprise.
Understand the standard
Cybersecurity standards provide guidelines for distinguishing between safety-critical and non-safety-critical components. According to ISA guidelines, security-critical assets and non-security-critical assets must be logically or physically divided into zones.
NAMUR provides a similar set of guidelines in worksheet NA163, "Security Risk Assessment for SIS." The guideline defines three logical areas-the core SIS, the extended SIS, and the control system architecture (which NAMUR calls "peripherals") and states that they must be physically or logically separate (Figure 1).
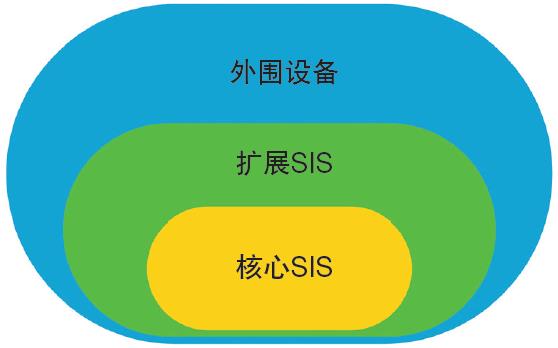
Figure 1: NAMUR provides a set of guidelines similar to the ISA62443 cybersecurity standard, where SIS functions are divided into three areas: core SIS, extended SIS, and control system architecture (which NAMUR calls "peripherals"). Image credit: Emerson
The core SIS consists of the devices needed to perform safety functions (logic solvers, input/output (I/O) devices, sensors, and terminal actuators). Extended SIS that contains safety system components not required to perform safety functions (for example, engineer stations). Peripherals are devices and systems such as basic process control systems (BPCS) that are not directly or indirectly assigned to SIS but can be used in the context of safety functions. Safety features may include resending requests from basic process control systems, or displaying safety features in the human-machine interface.
Neither standard clearly defines the required architecture. Users must decide how best to build the SIS network and ensure that adequate logical and physical isolation is provided between the basic process control system and the SIS in the final design. In general, companies have three options to build an SIS network:
●Separated SIS : Completely disconnected from and independent of the basic process control system;
●Interfaced SIS : Interface SIS is connected to the basic process control system via an industrial protocol (usually Modbus);
●Integrated SIS :Integrated SIS that is connected to the basic process control system, but needs to be sufficiently isolated to meet cybersecurity standards.
Some might argue that deploying an isolated SIS is more secure than any other type of SIS. However, as long as the security architecture is defined in advance and enforced during the design, implementation, and maintenance of the security system, all listed architectures can provide an enhanced security architecture. Although important, SIS architecture is only one aspect of a security system that defines security.
Use Defense in Depth
Protecting SIS requires a defense-in-depth approach. With cyberattacks increasing every year, a single layer of protection is not enough for safety-critical assets. Network administrators are employing multiple layers of security - antivirus, user management, multi-factor authentication, intrusion detection/prevention, whitelisting, firewalls, and more - to ensure that unauthorized users face insurmountable barriers to entry. The goal of the defense in depth strategy is to add access control protection mechanisms. This can be done by adding layers of protection that complement each other.
Isolated System
One of the most common ways to protect SIS is to isolate the system completely, creating a "quarantine" between the core SIS functions and the basic process control system (Figure 2). The benefits of this approach are obvious. If SIS is separated from other systems, security is strengthened by default to prevent intrusions.

Figure 2: Infrastructure with a buffer separating safety-critical and non-safety-critical SIS, but with additional maintenance to maintain a defense-in-depth security layer on two different systems.
However, even isolated systems are not immune to cyber attacks. Users ultimately need to access the system from the outside to perform tasks such as extracting event records for event analysis, bypassing, overwriting, validating test records, or performing configurations, changes, and applying security updates. USB drives, which are often used to implement these updates, are even less easy to secure.
Because of the dependency on external media, this is one of the main reasons why isolated SIS still requires additional layers of protection (as used to protect the basic process control system). Appropriate system hardening allows users to manage two separate defense in depth architectures. This makes it possible to increase working time, extend the time between outages, and increase the buffer area against inadvertent holes in the protective layer.
Interface System
The interface system functions like an isolation system. In an isolated system, security-related functions are physically separate from non-security-related functions (Figure 3). The interface system is distinguished by the fact that the basic process control system components and the core functions of SIS are connected through engineering links with industrial open protocols. Typically, firewalls or other security hardware and software limit the flow between the basic process control system and SIS.
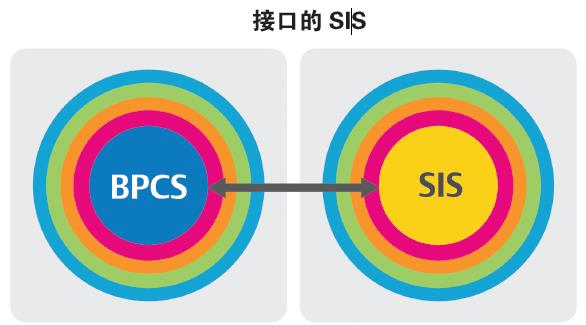
Figure 3: The interface architecture physically separates SIS from, but connects to, the basic process control system. This configuration typically requires the maintenance of multiple engineering connections and defense in depth systems.
Because the core SIS and extended SIS are physically separate from the peripherals, the interface system provides sufficient protection to meet the standards of ISA and NAMUR. However, just as in isolated systems, SIS hardware and software need to be protected. Users must ensure a connection to the extended SIS so that it does not compromise the core SIS.
In order to obtain this protection, the interface system requires that the Defense in Depth security layer be replicated on multiple systems. In some cases, multiple instances of network security that must be monitored may increase the effort required to maintain adequate security. End users should also ensure that the connection between the basic process control system and SIS is configured in a way that does not expose the system to risk.
Integrated System
Another option for implementing an isolation system is to integrate SIS (Figure 4). In this approach, SIS is integrated into the basic process control system, but there is a logical and physical separation between the core SIS and the extended SIS. Typically, this isolation is achieved using out-of-the-box embedded network security proprietary protocols. This eliminates many of the security risks that arise from manually designing the connection between SIS and the basic process control system.

Figure 4: In an integrated SIS architecture, safety-critical functions are logically and physically separated, but still located on the same system. This eliminates the need to maintain multiple defense systems in depth.
Integrated SIS requires the same level of defense-in-depth protection as isolated systems, but because some security layers need to protect both the basic process control system and SIS, integrated SIS can reduce the time and effort spent monitoring, updating, and maintaining the security layer. This approach provides protection beyond the normal layer of security. The integrated SIS also has other specific security layers designed to protect the core SIS.
By eliminating complex engineering interfaces between core and extended SIS through an integrated environment, factory acceptance testing (FAT) can be made simpler and faster, helping to bring projects online faster and with less rework.
Management Entrence
Careful consideration of layers of defense in depth is essential for SIS to provide cybersecurity, but it is not enough. To ensure that SIS networks have adequate security, organizations must also restrict entry points into safety-critical functions and take steps to mitigate any risks affecting those entry points.
The more entry points available for SIS's security-critical functions, the greater the opportunity for cyber attacks to exploit possible vulnerabilities in the security layer. While it is possible to adequately defend multiple intrusion points against intrusions, it would be easier and less resource-intensive to defend against only one intrusion point.
NAMUR provides clear guidance for the partitioned SIS architecture in the interface format (Figure 1). The core SIS, extended SIS, and control system architectures are properly isolated in their respective regions. Engineering connections between architectural elements (engineer stations, BPCS, plant information management systems, asset management systems, etc.) in the 3 regions can create multiple potential connection points to the core SIS.
These connection points are not inherently a security risk; It is generally assumed that they acquire adequate defense in depth. If each link requires security protection, you may need to manage five or more sets of security hardware and software.
The integrated SIS architecture can provide a design that limits entry points. The best integrated safety instrumentation systems are configured with a component that acts as a gateway for all traffic to and from critical safety functions, so that only one entry point needs to be defended, with the same layer of defense in depth that protects basic process control systems and some additional layers of protection dedicated to core SIS. This design reduces maintenance and monitoring while providing the same or even higher level of standard SIS isolation than other architectures.
There is often an assumption that more physical isolation between SIS and the basic process control system means more inherent security. However, as with buffers, more physical isolation can lead to increased maintenance and monitoring overhead in order to ensure adequate defense in depth. For enterprises, the additional cost limits the value of air-gapping - seeking to optimize performance and production while meeting network security standards. And try at the same time.
Integrated and interfacing systems enable a high level of connectivity while providing flexibility in implementing a defense-in-depth network security architecture. Because both architectures provide the highest level of security, implementation teams seeking to maintain a defendable SIS throughout the life cycle of the system often find that they have more options to choose between a basic process control system and SIS to meet unique enterprise goals.
From : Control Engineering Network
Author:Sergio Diaz
 沪公网安备31011502401909
沪公网安备31011502401909